Beware Facebook Scammers
Note that this is our official Facebook page (@wiglenet), anything else is a scam: https://www.facebook.com/wiglenet/
-bobzilla
GES (Global Edge Security) has been enabled for this environment and a GES CNAME has been generated
Properly setting the primary domain helps our system ensure your site serves traffic as expected. This domain should be the landing page for your visitors.
-bobzilla
Currently Analyzing X Wireless Receptors in your Network Airspace
AE is constantly working hard for you to monitor the airspace for wireless receptors”, constantly being the key word.
-bobzilla
Beware Facebook Scammers
Note that this is our official Facebook page (@wiglenet), anything else is a scam: https://www.facebook.com/wiglenet/
-bobzilla
Lorem Ipsum is simply dummy text of the printing and typesetting industry
It is a long established fact that a reader will be the readable content of a page when looking at its layout.
-bobzilla

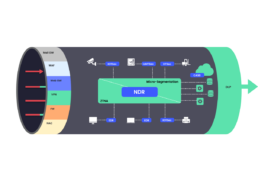
In a world of continuous network attacks
various security solutions are added to the network model.
Let the network be wired, wireless or even virtual such as SASE.
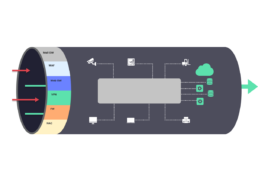
A prediction, prevention, detection and response framework used to provide attack protection and access protection for email
A traffic processing engine that is mainly focused on exploit mitigation, such as injection attacks (XSS and SQL injection) and application-level denial of service (DoS)
Will be added soon by Noa...
Products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls
Secures traffic bidirectionally across networks
Enables organizations to implement policies and control access to corporate infrastructure by user devices and cyber-physical devices such as IoT and operational technology (OT) devices
At the entry points
Preventive security solutions are stacked
to enforce that only legitimate traffic enters the network. The purpose of these solutions is to prevent initial compromise of servers and devices on the network and prevent traffic from unknown sources to reach corporate devices.
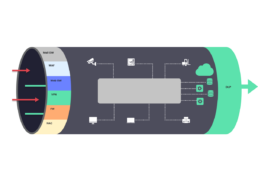
A prediction, prevention, detection and response framework used to provide attack protection and access protection for email
A traffic processing engine that is mainly focused on exploit mitigation, such as injection attacks (XSS and SQL injection) and application-level denial of service (DoS)
Will be added soon by Noa...
Products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls
Secures traffic bidirectionally across networks
Enables organizations to implement policies and control access to corporate infrastructure by user devices and cyber-physical devices such as IoT and operational technology (OT) devices
Offerings that provide visibility into data usage and movement across an organization, as well as dynamic enforcement of security policies based on content and context at the time of actions on data
At the exit points
DLP solutions are placed
to ensure that only policy-allowed data leaves the corporate.
A prediction, prevention, detection and response framework used to provide attack protection and access protection for email
A traffic processing engine that is mainly focused on exploit mitigation, such as injection attacks (XSS and SQL injection) and application-level denial of service (DoS)
Will be added soon by Noa...
Products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls
Secures traffic bidirectionally across networks
Enables organizations to implement policies and control access to corporate infrastructure by user devices and cyber-physical devices such as IoT and operational technology (OT) devices
Offerings that provide visibility into data usage and movement across an organization, as well as dynamic enforcement of security policies based on content and context at the time of actions on data
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Addresses software, hardware, and network and data protection requirements for the HDO’s IoMT devices
The practices and technologies used to protect people, assets and information involved in the monitoring and/or control of physical devices, processes and events, particularly in production and operations
Endpoint solutions that detect and investigate security events, contain attacks and produce remediation guidance.
A platform that integrates, correlates and contextualizes data and alerts from multiple security prevention, detection and response components.
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Products and services that address security gaps in an organization’s use of cloud services
While the above solutions
serve as an initial gatekeeper
additional security solutions are deployed for when an attacker has already established a foothold within the organization.
A prediction, prevention, detection and response framework used to provide attack protection and access protection for email
A traffic processing engine that is mainly focused on exploit mitigation, such as injection attacks (XSS and SQL injection) and application-level denial of service (DoS)
Will be added soon by Noa...
Products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls
Secures traffic bidirectionally across networks
Enables organizations to implement policies and control access to corporate infrastructure by user devices and cyber-physical devices such as IoT and operational technology (OT) devices
Offerings that provide visibility into data usage and movement across an organization, as well as dynamic enforcement of security policies based on content and context at the time of actions on data
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Addresses software, hardware, and network and data protection requirements for the HDO’s IoMT devices
The practices and technologies used to protect people, assets and information involved in the monitoring and/or control of physical devices, processes and events, particularly in production and operations
Endpoint solutions that detect and investigate security events, contain attacks and produce remediation guidance.
A platform that integrates, correlates and contextualizes data and alerts from multiple security prevention, detection and response components.
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Products and services that address security gaps in an organization’s use of cloud services
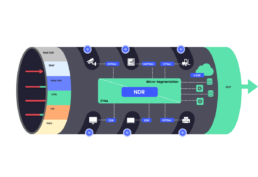
The wireless capabilities
of the devices on the network
changes the above illustration
A prediction, prevention, detection and response framework used to provide attack protection and access protection for email
A traffic processing engine that is mainly focused on exploit mitigation, such as injection attacks (XSS and SQL injection) and application-level denial of service (DoS)
Will be added soon by Noa...
Products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls
Secures traffic bidirectionally across networks
Enables organizations to implement policies and control access to corporate infrastructure by user devices and cyber-physical devices such as IoT and operational technology (OT) devices
Offerings that provide visibility into data usage and movement across an organization, as well as dynamic enforcement of security policies based on content and context at the time of actions on data
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Addresses software, hardware, and network and data protection requirements for the HDO’s IoMT devices
The practices and technologies used to protect people, assets and information involved in the monitoring and/or control of physical devices, processes and events, particularly in production and operations
Endpoint solutions that detect and investigate security events, contain attacks and produce remediation guidance.
A platform that integrates, correlates and contextualizes data and alerts from multiple security prevention, detection and response components.
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Products and services that address security gaps in an organization’s use of cloud services
These open up a new attack surface
uncovered by existing security solutions.
While wireless capable devices are connected securely to the corporate network (whether wired or wireless), they are inherently open to accepting and processing network traffic transmitted by any other device in their proximity.
They are also capable of sending out insecure network traffic.
![]()
In essence, today’s corporate network is perforated with gaps generated by these corporate-owned dual-connected devices, aka Wireless Receptors.
A prediction, prevention, detection and response framework used to provide attack protection and access protection for email
A traffic processing engine that is mainly focused on exploit mitigation, such as injection attacks (XSS and SQL injection) and application-level denial of service (DoS)
Will be added soon by Noa...
Products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls
Secures traffic bidirectionally across networks
Enables organizations to implement policies and control access to corporate infrastructure by user devices and cyber-physical devices such as IoT and operational technology (OT) devices
Offerings that provide visibility into data usage and movement across an organization, as well as dynamic enforcement of security policies based on content and context at the time of actions on data
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Addresses software, hardware, and network and data protection requirements for the HDO’s IoMT devices
The practices and technologies used to protect people, assets and information involved in the monitoring and/or control of physical devices, processes and events, particularly in production and operations
Endpoint solutions that detect and investigate security events, contain attacks and produce remediation guidance.
A platform that integrates, correlates and contextualizes data and alerts from multiple security prevention, detection and response components.
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Products and services that address security gaps in an organization’s use of cloud services
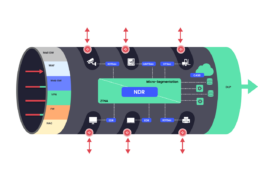
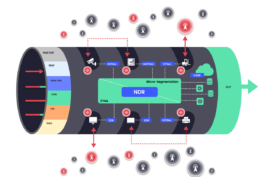
Wireless Receptors
also create internal insecure network paths.
These internal networks, called Shadow Networks, additionally defeat micro-segmentation solutions.
A prediction, prevention, detection and response framework used to provide attack protection and access protection for email
A traffic processing engine that is mainly focused on exploit mitigation, such as injection attacks (XSS and SQL injection) and application-level denial of service (DoS)
Will be added soon by Noa...
Products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls
Secures traffic bidirectionally across networks
Enables organizations to implement policies and control access to corporate infrastructure by user devices and cyber-physical devices such as IoT and operational technology (OT) devices
Offerings that provide visibility into data usage and movement across an organization, as well as dynamic enforcement of security policies based on content and context at the time of actions on data
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Addresses software, hardware, and network and data protection requirements for the HDO’s IoMT devices
The practices and technologies used to protect people, assets and information involved in the monitoring and/or control of physical devices, processes and events, particularly in production and operations
Endpoint solutions that detect and investigate security events, contain attacks and produce remediation guidance.
A platform that integrates, correlates and contextualizes data and alerts from multiple security prevention, detection and response components.
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Products and services that address security gaps in an organization’s use of cloud services
The corporate network
is surrounded by an infinite number of Antenna for Hire.
These are wireless devices that broadcast in the corporate network. These can be laptops, open-source Access Points (openWRT), the wireless router in a neighboring cafe, personal mobile phones, OT and IoT devices such as Wifi cameras, TVs, monitors, A/C units, etc.
![]()
Today’s attack tools can compromise an Antenna for Hire remotely and through software-based tools. From there the attacker can connect wirelessly to the Wireless Receptor and penetrate the network or act as an exfiltration destination.
A prediction, prevention, detection and response framework used to provide attack protection and access protection for email
A traffic processing engine that is mainly focused on exploit mitigation, such as injection attacks (XSS and SQL injection) and application-level denial of service (DoS)
Will be added soon by Noa...
Products and services used to achieve security and confidentiality for data in motion by means of encryption and access controls
Secures traffic bidirectionally across networks
Enables organizations to implement policies and control access to corporate infrastructure by user devices and cyber-physical devices such as IoT and operational technology (OT) devices
Offerings that provide visibility into data usage and movement across an organization, as well as dynamic enforcement of security policies based on content and context at the time of actions on data
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Addresses software, hardware, and network and data protection requirements for the HDO’s IoMT devices
The practices and technologies used to protect people, assets and information involved in the monitoring and/or control of physical devices, processes and events, particularly in production and operations
Endpoint solutions that detect and investigate security events, contain attacks and produce remediation guidance.
A platform that integrates, correlates and contextualizes data and alerts from multiple security prevention, detection and response components.
Addresses software, hardware, network and data protection for vendors bringing IoT solutions to market, as well as end users using them
Products and services that address security gaps in an organization’s use of cloud services
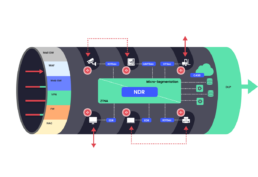
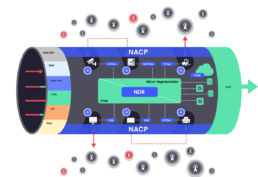
Network Airspace Control and Protection (NACP)
is an additional network security layer
that closes these wireless holes. The NACP prevents the over-the-air attack from entering and exiting the corporate network as well as extends network and micro segmentation by preventing over- the-air lateral movement.